So last week on Amazon there was a sale for this 5 TB Western Digital Drive for $99.99 plus tax.

I purchased this primarily to backup files and bring them to work. Having 5TB in a small package seemed cool.
But there was another side thing that was interesting, this drive had hardware encryption. I believe I have had several Western Digital drives for the Element line that did not have encryption, and I would either use Truecrypt (which works/worked in both Windows and Linux but no longer supported), Bitlocker (Windows Only) or LUKS(Linux only). I know there are other options like GPG that work in both environments, but I was wondering if this hardware encryption could work in both Linux and Windows. The primary goal of this purchase was a 5TB drive, but the encryption was kind of a cool thing to have.
So lets take a look at it.
When I first got the drive I plugged it in my PC and saw the drive and it was not encrypted. There were two files in there
E:\Install Discovery for Mac.dmg
E:\Install Discovery for Windows.exe
I run the Windows executable and a little applet appears in my system tray (bottom right)

Expanding it give this
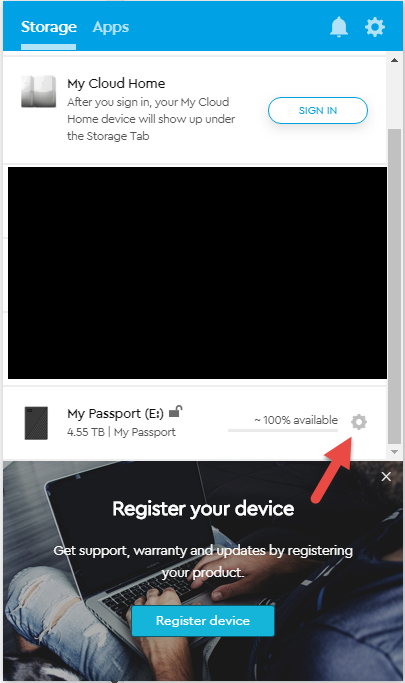
Note that when I first started this up, that little gear icon was not there, and that Register your device part was not there either, this thing wanted to talk to the Internet to download other things and my network based firewall was blocking it. I allowed it to download and got this. This to me is pretty shady.
So I now can lock it.
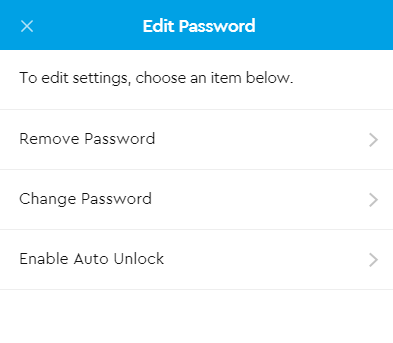
Looks like you can cache the password to have it automatically unlock when you reattach this drive.
This is how it looks like when you move it to another machine.
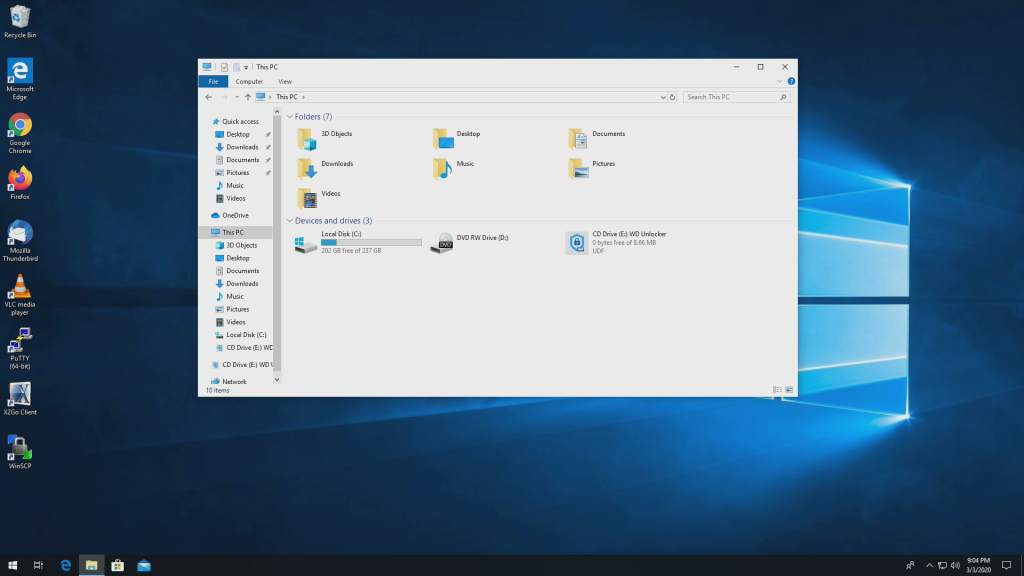
Click on the CD ROM and you get this
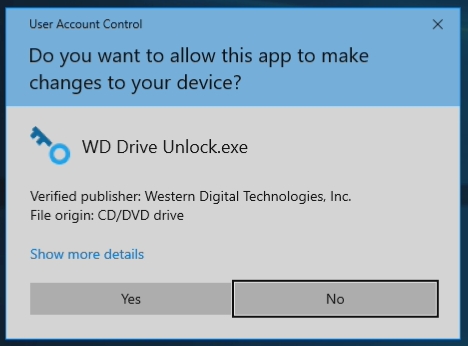
Click Yes and you are prompted for the password
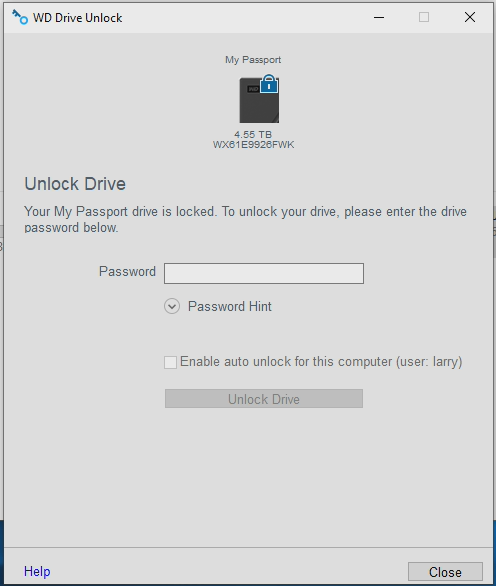
Type in the password and you are able to unlock see the contents
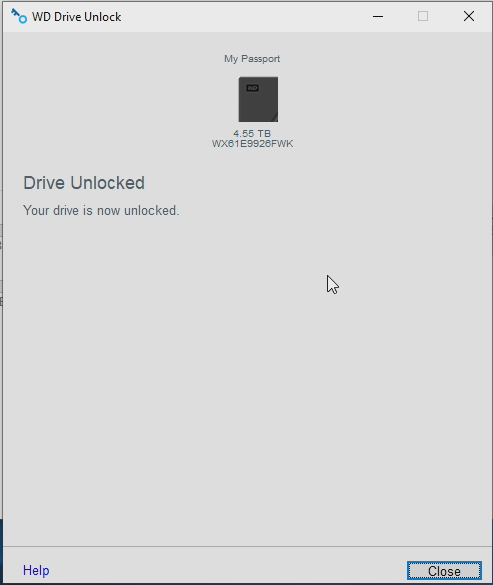
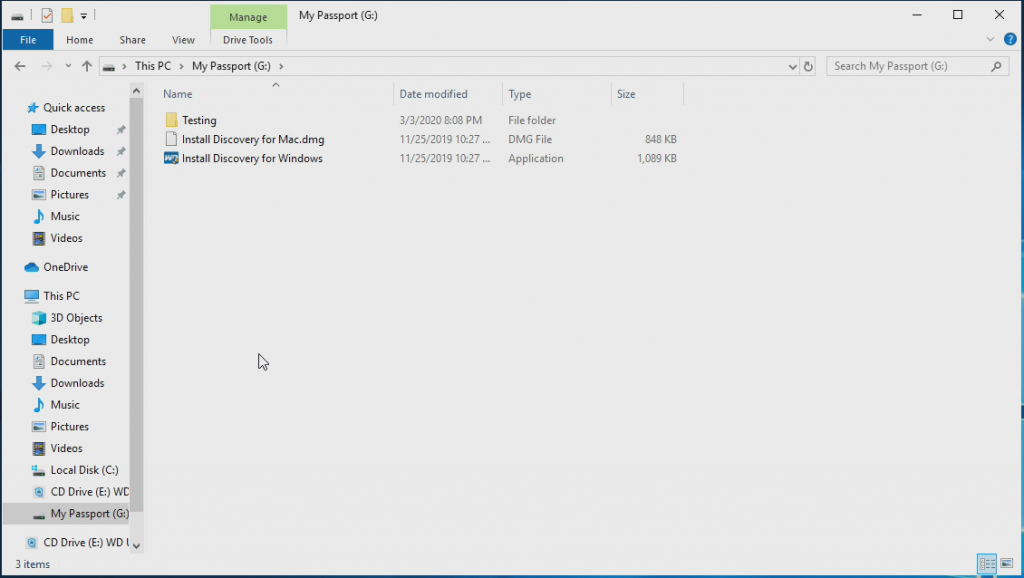
So can we do this in Linux, CentOS 7?
Yes you can
First of all make sure you have NTFS support
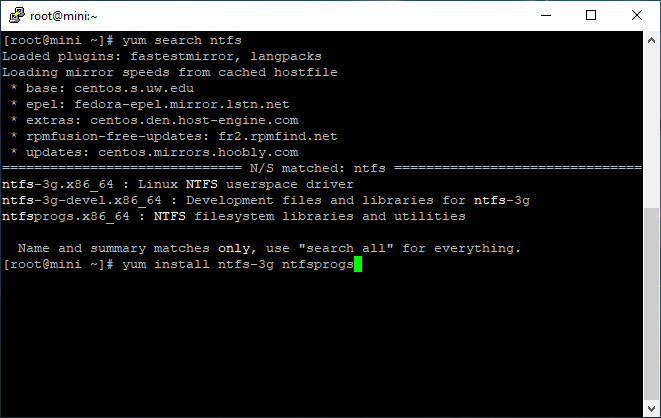
I suspect once mounted you can format to EXT3 but since I want to access this from both Windows and Linux I will leave it at NTFS.
yum install ntfs-3g ntfsprogs
Next you will need some supporting python packages, note that the software works only with python 2, I think I can get it to work with the more modern python 3, but for now lets just get it to work with python 2.
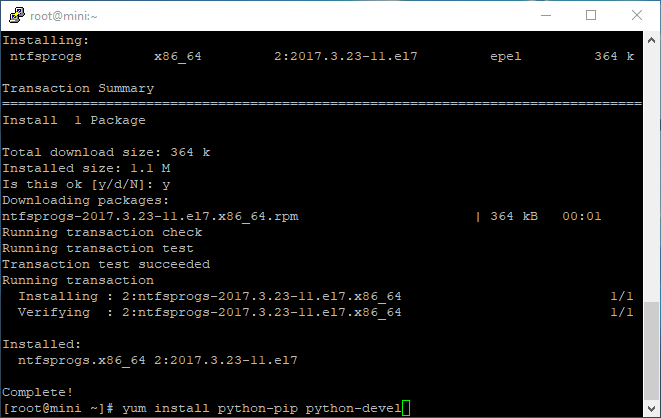
So you will need python-ip and python-devel
Next you will need a python module, use the pip installer to get it
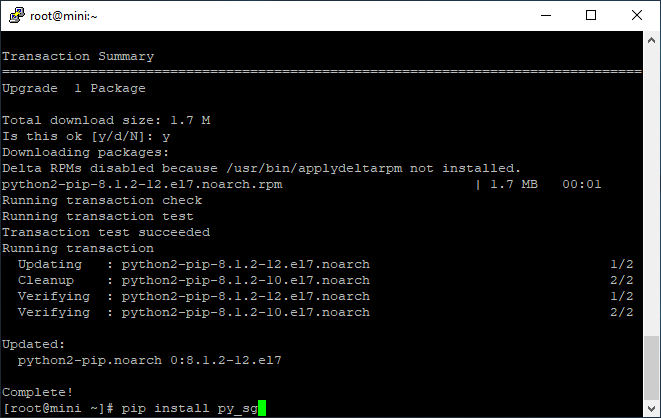
Then download the actual python script used to decrypt the drive
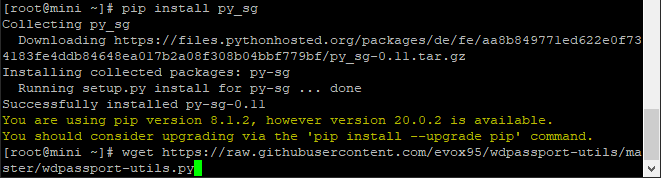
wget https://raw.githubusercontent.com/evox95/wdpassport-utils/master/wdpassport-utils.py
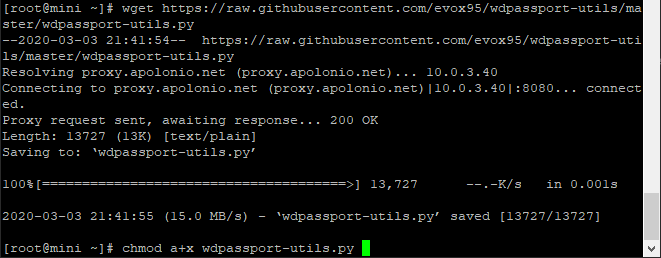
Make it executable
Before we continue run cat /proc/partitions to see what drives are there
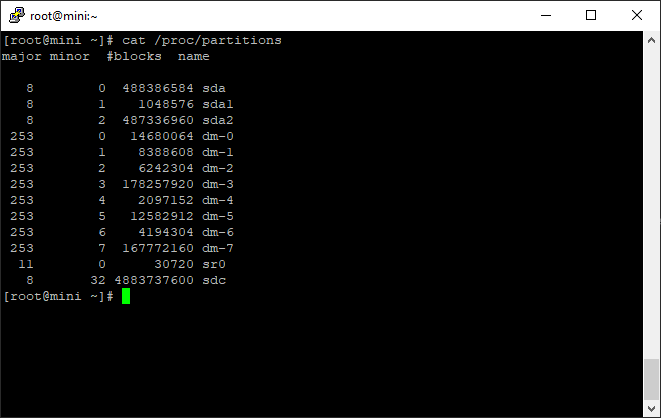
Note the sdc device with no other partitions.
Now run the executable with the -s flag to show status
./wdpassport-utils.py -s
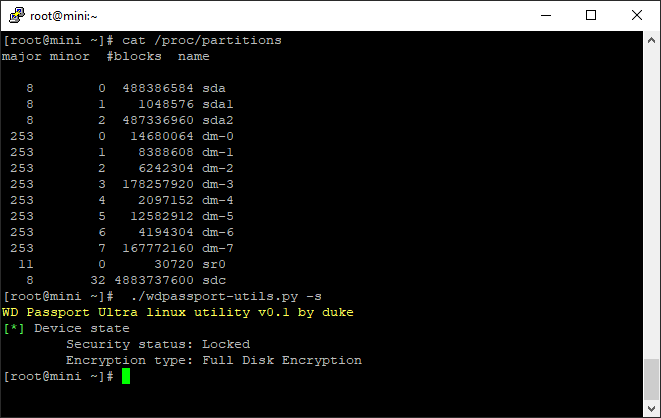
Note the sr0 device, you could mount that read only and it would be the bits to unlock it in Windows, a file called WD Drive Unlock.exe
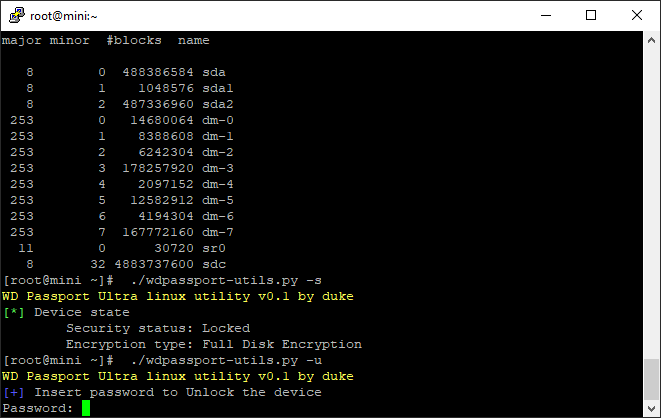
No run the command to unlock it with -u
Drive is not unlocked and you will have an sdc1 device you can mount
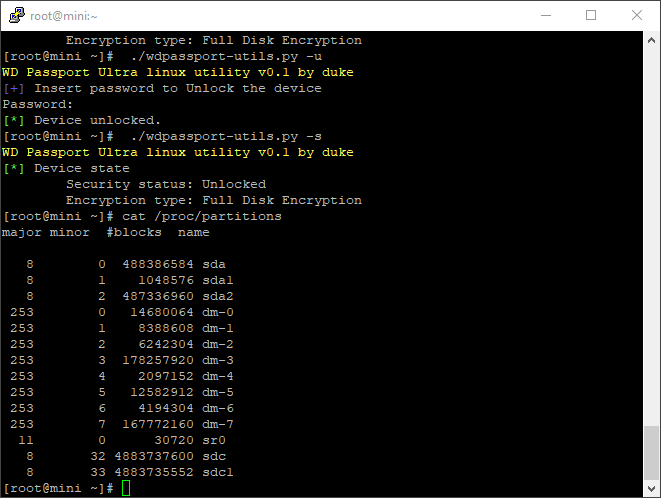
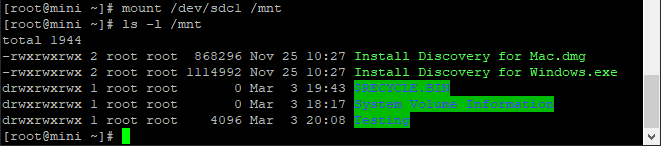
Pretty cool, if you were to umount it and look at it again on your windows box it would be locked.
Couple things I learned about this drive online
- The drive itself is encrypted, remove the drive and putting it in a new USB to SATA connecter will not decrypt the contents.
- You can brute force the password, try and try and try., probably script it.
- Even if you don’t set a password, you cannot mount the drive in another device.
- You can brick this drive
- I do not know how well this drive holds up to pros trying to break in.
So, for my use case, an offsite backup, it will work, if I add additional encryption to whatever sensitive I land on this drive, and not so sensitive I can probably just use the hardware encryption.
Kind of cool.
Weight: 301.6
